Question # 1
Refer to the exhibit.
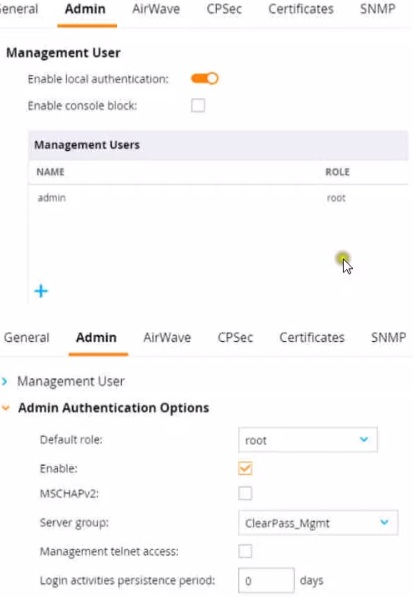
This Aruba Mobility Controller (MC) should authenticate managers who access the Web Ul
to ClearPass Policy Manager (CPPM) ClearPass admins have asked you to use RADIUS
and explained that the MC should accept managers' roles in Aruba-Admin-Role VSAs.
Which setting should you change to follow Aruba best security practices? | | A. Change the local user role to read-only | | B. Clear the MSCHAP check box | | C. Disable local authentication | | D. Change the default role to "guest-provisioning" |
C. Disable local authentication
Explanation: For following Aruba best security practices, the setting you should change is
to disable local authentication. When integrating with an external RADIUS server like
ClearPass Policy Manager (CPPM) for authenticating administrative access to the Mobility
Controller (MC), it is a best practice to rely on the external server rather than the local user
database. This practice not only centralizes the management of user roles and access but
also enhances security by leveraging CPPM's advanced authentication mechanisms.
Question # 2
| Device A is contacting https://arubapedia.arubanetworks.com. The web server sends a
certificate chain. What does the browser do as part of validating the web server certificate? | | A. It makes sure that the key in the certificate matches the key that DeviceA uses for
HTTPS. | | B. It makes sure the certificate has a DNS SAN that matches
arubapedia.arubanetworks.com | | C. It makes sure that the public key in the certificate matches DeviceA's private HTTPS
key. | | D. It makes sure that the public key in the certificate matches a private key stored on
DeviceA. |
B. It makes sure the certificate has a DNS SAN that matches
arubapedia.arubanetworks.com
Explanation: When a device like Device A contacts a secure website and receives a
certificate chain from the server, the browser's primary task is to validate the web server's
certificate to ensure it is trustworthy. Part of this validation includes checking that the
certificate contains a DNS Subject Alternative Name (SAN) that matches the domain name
of the website being accessed—in this case, arubapedia.arubanetworks.com. This ensures
that the certificate was indeed issued to the entity operating the domain and helps prevent
man-in-the-middle attacks where an invalid certificate could be presented by an attacker.
The DNS SAN check is critical because it directly ties the digital certificate to the domain it
secures, confirming the authenticity of the website to the user's browser.
Question # 3
| You are configuring ArubaOS-CX switches to tunnel client traffic to an Aruba Mobility Controller (MC). What should you do to enhance security for control channel communications between the switches and the MC?
| | A. Create one UBT zone for control traffic and a second UBT zone for clients.
| | B. Configure a long, random PAPI security key that matches on the switches and the MC.
| | C. install certificates on the switches, and make sure that CPsec is enabled on the MC
| | D. Make sure that the UBT client vlan is assigned to the interface on which the switches reach the MC and only that interface.
|
B. Configure a long, random PAPI security key that matches on the switches and the MC.
Question # 4
What are some functions of an AruDaOS user role?
| A. The role determines which authentication methods the user must pass to gain network access
| B. The role determines which firewall policies and bandwidth contract apply to the clients traffic
| C. The role determines which wireless networks (SSiDs) a user is permitted to access
| D. The role determines which control plane ACL rules apply to the client's traffic
|
B. The role determines which firewall policies and bandwidth contract apply to the clients traffic
Explanation:
An ArubaOS user role determines the firewall policies and bandwidth contracts that apply to the client’s traffic. When a user is authenticated, they are assigned a role, and this role has associated policies that govern network access rights, Quality of Service (QoS), Layer 2 forwarding, Layer 3 routing behaviors, and bandwidth contracts for users or devices.
References:
• Aruba Networks official documentation on user roles in ArubaOS.
• Technical guides that detail user role definitions and their impact on network policies.
Question # 5
A company with 439 employees wants to deploy an open WLAN for guests. The company wants the experience to be as follows:
*Guests select the WLAN and connect without having to enter a password.
*Guests are redirected to a welcome web page and log in.
The company also wants to provide encryption for the network for devices that are capable. Which security options should you implement for the WLAN? | | A. Opportunistic Wireless Encryption (OWE) and WPA3-Personal
| | B. WPA3-Personal and MAC-Auth
| | C. Captive portal and Opportunistic Wireless Encryption (OWE) in transition mode
| | D. Captive portal and WPA3-Personal
|
C. Captive portal and Opportunistic Wireless Encryption (OWE) in transition mode
Question # 6
| What is a use case for implementing RadSec instead of RADIUS?
| | A. A university wants to protect communications between the students' devices and the network access server.
| | B. A corporation wants to implement EAP-TLS to authenticate wireless users at their main office.
| | C. A school district wants to protect messages sent between RADIUS clients and servers over an untrusted network.
| | D. A organization wants to strengthen the encryption used to protect RADIUS communications without increasing complexity.
|
C. A school district wants to protect messages sent between RADIUS clients and servers over an untrusted network.
Question # 7
| What are the roles of 802.1X authenticators and authentication servers? | | A. The authenticator stores the user account database, while the server stores access
policies. | | B. The authenticator supports only EAP, while the authentication server supports only
RADIUS. | | C. The authenticator is a RADIUS client and the authentication server is a RADIUS server. | | D. The authenticator makes access decisions and the server communicates them to the
supplicant. |
C. The authenticator is a RADIUS client and the authentication server is a RADIUS server.
Explanation: In the 802.1X network access control model, the roles of the authenticator
and the authentication server are distinct yet complementary. The authenticator acts as a
RADIUS client, which is a network device, like a switch or wireless access point, that
directly interfaces with the client machine (supplicant). The authentication server, typically a
RADIUS server, is responsible for verifying the credentials provided by the supplicant
through the authenticator. This setup helps in separating the duties where the authenticator
enforces authentication but does not decide on the validity of the credentials, which is the
role of the authentication server.
HP HPE6-A78 Exam Dumps
5 out of 5
Pass Your Aruba Certified Network Security Associate Exam in First Attempt With HPE6-A78 Exam Dumps. Real Aruba-ACNSA Exam Questions As in Actual Exam!
— 167 Questions With Valid Answers
— Updation Date : 15-Apr-2025
— Free HPE6-A78 Updates for 90 Days
— 98% Aruba Certified Network Security Associate Exam Passing Rate
PDF Only Price 49.99$
19.99$
Buy PDF
Speciality
Additional Information
Testimonials
Related Exams
- Number 1 HP Aruba-ACNSA study material online
- Regular HPE6-A78 dumps updates for free.
- Aruba Certified Network Security Associate Practice exam questions with their answers and explaination.
- Our commitment to your success continues through your exam with 24/7 support.
- Free HPE6-A78 exam dumps updates for 90 days
- 97% more cost effective than traditional training
- Aruba Certified Network Security Associate Practice test to boost your knowledge
- 100% correct Aruba-ACNSA questions answers compiled by senior IT professionals
HP HPE6-A78 Braindumps
Realbraindumps.com is providing Aruba-ACNSA HPE6-A78 braindumps which are accurate and of high-quality verified by the team of experts. The HP HPE6-A78 dumps are comprised of Aruba Certified Network Security Associate questions answers available in printable PDF files and online practice test formats. Our best recommended and an economical package is Aruba-ACNSA PDF file + test engine discount package along with 3 months free updates of HPE6-A78 exam questions. We have compiled Aruba-ACNSA exam dumps question answers pdf file for you so that you can easily prepare for your exam. Our HP braindumps will help you in exam. Obtaining valuable professional HP Aruba-ACNSA certifications with HPE6-A78 exam questions answers will always be beneficial to IT professionals by enhancing their knowledge and boosting their career.
Yes, really its not as tougher as before. Websites like Realbraindumps.com are playing a significant role to make this possible in this competitive world to pass exams with help of Aruba-ACNSA HPE6-A78 dumps questions. We are here to encourage your ambition and helping you in all possible ways. Our excellent and incomparable HP Aruba Certified Network Security Associate exam questions answers study material will help you to get through your certification HPE6-A78 exam braindumps in the first attempt.
Pass Exam With HP Aruba-ACNSA Dumps. We at Realbraindumps are committed to provide you Aruba Certified Network Security Associate braindumps questions answers online. We recommend you to prepare from our study material and boost your knowledge. You can also get discount on our HP HPE6-A78 dumps. Just talk with our support representatives and ask for special discount on Aruba-ACNSA exam braindumps. We have latest HPE6-A78 exam dumps having all HP Aruba Certified Network Security Associate dumps questions written to the highest standards of technical accuracy and can be instantly downloaded and accessed by the candidates when once purchased. Practicing Online Aruba-ACNSA HPE6-A78 braindumps will help you to get wholly prepared and familiar with the real exam condition. Free Aruba-ACNSA exam braindumps demos are available for your satisfaction before purchase order.
Send us mail if you want to check HP HPE6-A78 Aruba Certified Network Security Associate DEMO before your purchase and our support team will send you in email.
If you don't find your dumps here then you can request what you need and we shall provide it to you.
Bulk Packages
$50
- Get 3 Exams PDF
- Get $33 Discount
- Mention Exam Codes in Payment Description.
Buy 3 Exams PDF
$70
- Get 5 Exams PDF
- Get $65 Discount
- Mention Exam Codes in Payment Description.
Buy 5 Exams PDF
$100
- Get 5 Exams PDF + Test Engine
- Get $105 Discount
- Mention Exam Codes in Payment Description.
Buy 5 Exams PDF + Engine
 Jessica Doe
Aruba-ACNSA
We are providing HP HPE6-A78 Braindumps with practice exam question answers. These will help you to prepare your Aruba Certified Network Security Associate exam. Buy Aruba-ACNSA HPE6-A78 dumps and boost your knowledge.
|
