Question # 1
Context:
Cluster: prod
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context prod
Task:
Analyse and edit the given Dockerfile (based on the ubuntu:18:04 image)
/home/cert_masters/Dockerfile fixing two instructions present in the file being prominent security/best-practice issues.
Analyse and edit the given manifest file
/home/cert_masters/mydeployment.yaml fixing two fields present in the file being prominent security/best-practice issues.
Note: Don't add or remove configuration settings; only modify the existing configuration settings, so that two configuration settings each are no longer security/best-practice concerns.
Should you need an unprivileged user for any of the tasks, use user nobody with user id 65535 |
Explanation:
1. For Dockerfile: Fix the image version & user name in Dockerfile2. For mydeployment.yaml : Fix security contexts
Explanation[desk@cli] $ vim /home/cert_masters/Dockerfile
FROM ubuntu:latest # Remove this
FROM ubuntu:18.04 # Add this
USER root # Remove this
USER nobody # Add this
RUN apt get install -y lsof=4.72 wget=1.17.1 nginx=4.2
ENV ENVIRONMENT=testing
USER root # Remove this
USER nobody # Add this
CMD ["nginx -d"] 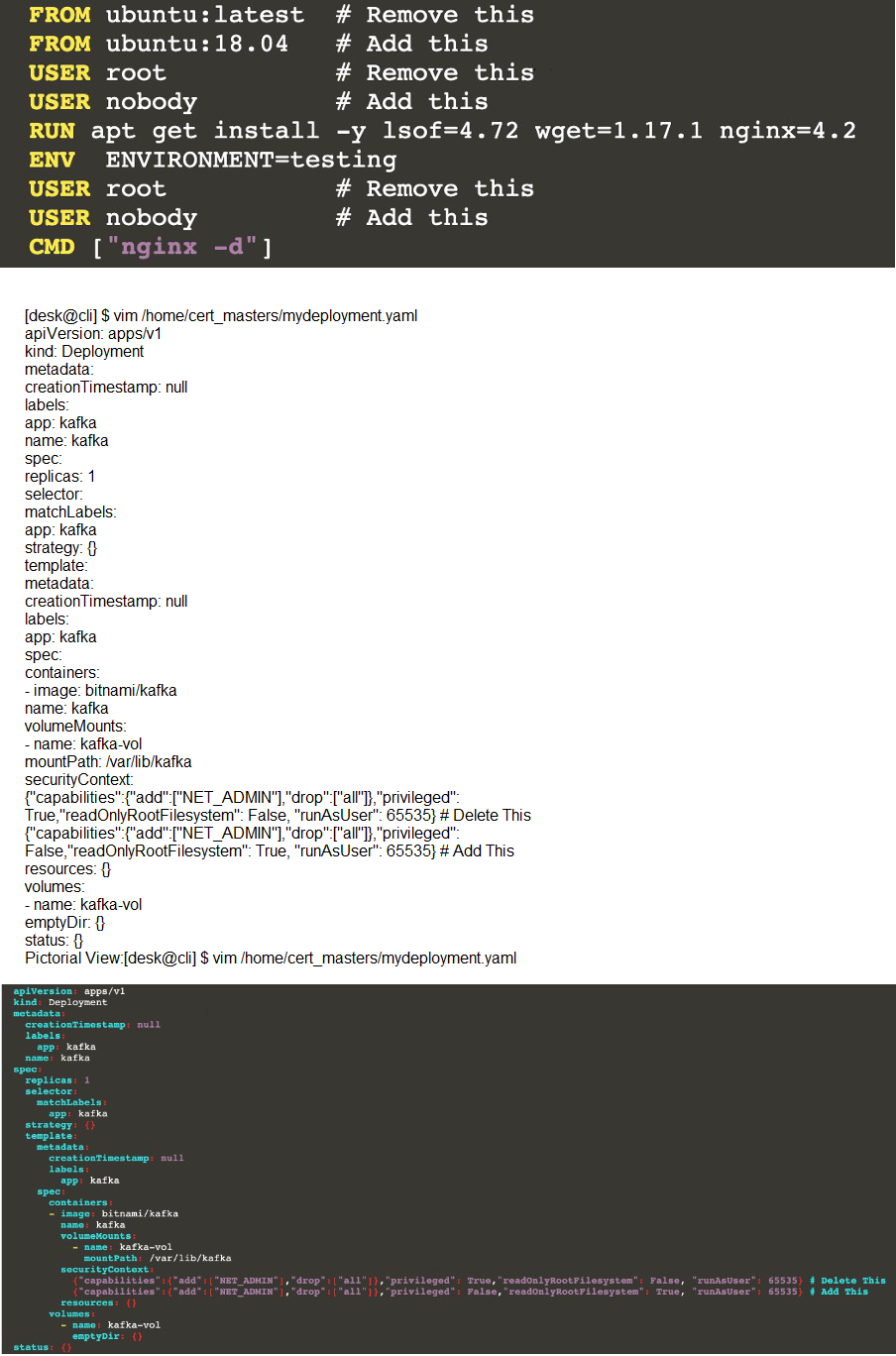
Question # 2
| Create a Pod name Nginx-pod inside the namespace testing, Create a service for the
Nginx-pod named nginx-svc, using the ingress of your choice, run the ingress on tls, secure
port. |
Explanation:
$ kubectl get ing -n
NAME HOSTS ADDRESS PORTS AGE
cafe-ingress cafe.com 10.0.2.15 80 25s
$ kubectl describe ing -n
Name: cafe-ingress
Namespace: default
Address: 10.0.2.15
Default backend: default-http-backend:80 (172.17.0.5:8080)
Rules:
Host Path Backends
---- ---- --------
cafe.com
/tea tea-svc:80 ()
/coffee coffee-svc:80 ()
Annotations:
kubectl.kubernetes.io/last-applied-configuration:
{"apiVersion":"networking.k8s.io/v1","kind":"Ingress","metadata":{"annotations":{},"name":"c
afeingress","
namespace":"default","selfLink":"/apis/networking/v1/namespaces/default/ingress
es/cafeingress"},"
spec":{"rules":[{"host":"cafe.com","http":{"paths":[{"backend":{"serviceName":"teasvc","
servicePort":80},"path":"/tea"},{"backend":{"serviceName":"coffeesvc","
servicePort":80},"path":"/coffee"}]}}]},"status":{"loadBalancer":{"ingress":[{"ip":"169.48.
142.110"}]}}}
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal CREATE 1m ingress-nginx-controller Ingress default/cafe-ingress
Normal UPDATE 58s ingress-nginx-controller Ingress default/cafe-ingress
$ kubectl get pods -n
NAME READY STATUS RESTARTS AGE
ingress-nginx-controller-67956bf89d-fv58j 1/1 Running 0 1m
$ kubectl logs -n ingress-nginx-controller-67956bf89d-fv58j
-------------------------------------------------------------------------------
NGINX Ingress controller
Release: 0.14.0
Build: git-734361d
Repository: https://github.com/kubernetes/ingress-nginx
-------------------------------------------------------------------------------
Question # 3
Analyze and edit the given Dockerfile
FROM ubuntu:latest
RUN apt-get update -y
RUN apt-install nginx -y
COPY entrypoint.sh /
ENTRYPOINT ["/entrypoint.sh"]
USER ROOT
Fixing two instructions present in the file being prominent security best practice issues
Analyze and edit the deployment manifest file
apiVersion: v1
kind: Pod
metadata:
name: security-context-demo-2
spec:
securityContext:
runAsUser: 1000
containers:
- name: sec-ctx-demo-2
image: gcr.io/google-samples/node-hello:1.0
securityContext:
runAsUser: 0
privileged: True
allowPrivilegeEscalation: false
Fixing two fields present in the file being prominent security best practice issues
Don't add or remove configuration settings; only modify the existing configuration settings
Whenever you need an unprivileged user for any of the tasks, use user test-user with the
user id 5487 |
Explanation:
FROM debian:latest
MAINTAINER k@bogotobogo.com
# 1 - RUN
RUN apt-get update && DEBIAN_FRONTEND=noninteractive apt-get install -yq apt-utils
RUN DEBIAN_FRONTEND=noninteractive apt-get install -yq htop
RUN apt-get clean
# 2 - CMD
#CMD ["htop"]
#CMD ["ls", "-l"]
# 3 - WORKDIR and ENV
WORKDIR /root
ENV DZ version1
$ docker image build -t bogodevops/demo .
Sending build context to Docker daemon 3.072kB
Step 1/7 : FROM debian:latest
---> be2868bebaba
Step 2/7 : MAINTAINER k@bogotobogo.com
---> Using cache
---> e2eef476b3fd
Step 3/7 : RUN apt-get update && DEBIAN_FRONTEND=noninteractive apt-get install -yq
apt-utils
---> Using cache
---> 32fd044c1356
Step 4/7 : RUN DEBIAN_FRONTEND=noninteractive apt-get install -yq htop
---> Using cache
---> 0a5b514a209e
Step 5/7 : RUN apt-get clean
---> Using cache
---> 5d1578a47c17
Step 6/7 : WORKDIR /root
---> Using cache
---> 6b1c70e87675
Step 7/7 : ENV DZ version1
---> Using cache
---> cd195168c5c7
Successfully built cd195168c5c7
Successfully tagged bogodevops/demo:latest
Question # 4
Create a PSP that will only allow the persistentvolumeclaim as the volume type in the namespace restricted.
Create a new PodSecurityPolicy named prevent-volume-policy which prevents the pods which is having different volumes mount apart from persistentvolumeclaim.
Create a new ServiceAccount named psp-sa in the namespace restricted.
Create a new ClusterRole named psp-role, which uses the newly created Pod Security Policy prevent-volume-policy
Create a new ClusterRoleBinding named psp-role-binding, which binds the created ClusterRole psp-role to the created SA psp-sa.
Hint:
Also, Check the Configuration is working or not by trying to Mount a Secret in the pod maifest, it should get failed.
POD Manifest:
apiVersion: v1
kind: Pod
metadata:
name:
spec:
containers:
- name:
image:
volumeMounts:
- name:
mountPath:
volumes:
- name:
secret:
secretName: |
Explanation:
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
name: restricted
annotations:
seccomp.security.alpha.kubernetes.io/allowedProfileNames:
'docker/default,runtime/default'
apparmor.security.beta.kubernetes.io/allowedProfileNames: 'runtime/default'
seccomp.security.alpha.kubernetes.io/defaultProfileName: 'runtime/default'
apparmor.security.beta.kubernetes.io/defaultProfileName: 'runtime/default'
spec:
privileged: false
# Required to prevent escalations to root.
allowPrivilegeEscalation: false
# This is redundant with non-root + disallow privilege escalation,
# but we can provide it for defense in depth.
requiredDropCapabilities:
- ALL
# Allow core volume types.
volumes:
- 'configMap'
- 'emptyDir'
- 'projected'
- 'secret'
- 'downwardAPI'
# Assume that persistentVolumes set up by the cluster admin are safe to use.
- 'persistentVolumeClaim'
hostNetwork: false
hostIPC: false
hostPID: false
runAsUser:
# Require the container to run without root privileges.
rule: 'MustRunAsNonRoot'
seLinux:
# This policy assumes the nodes are using AppArmor rather than SELinux.
rule: 'RunAsAny'
supplementalGroups:
rule: 'MustRunAs'
ranges:
# Forbid adding the root group.
- min: 1
max: 65535
fsGroup:
rule: 'MustRunAs'
ranges:
# Forbid adding the root group.
- min: 1
max: 65535
readOnlyRootFilesystem: false
Question # 5
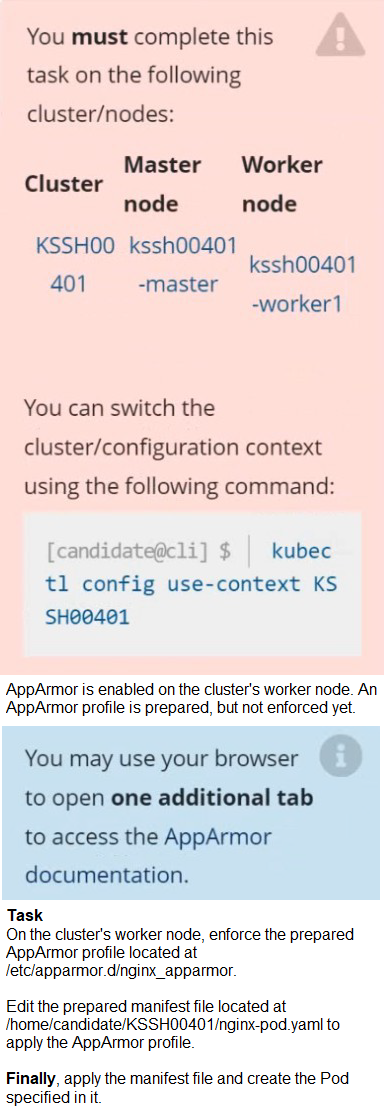 |
Question # 6
Cluster: scanner
Master node: controlplane
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context scanner
Given:
You may use Trivy's documentation.
Task:
Use the Trivy open-source container scanner to detect images with severe vulnerabilities used by Pods in the namespace nato.
Look for images with High or Critical severity vulnerabilities and delete the Pods that use those images.
Trivy is pre-installed on the cluster's master node. Use cluster's master node to use Trivy. |
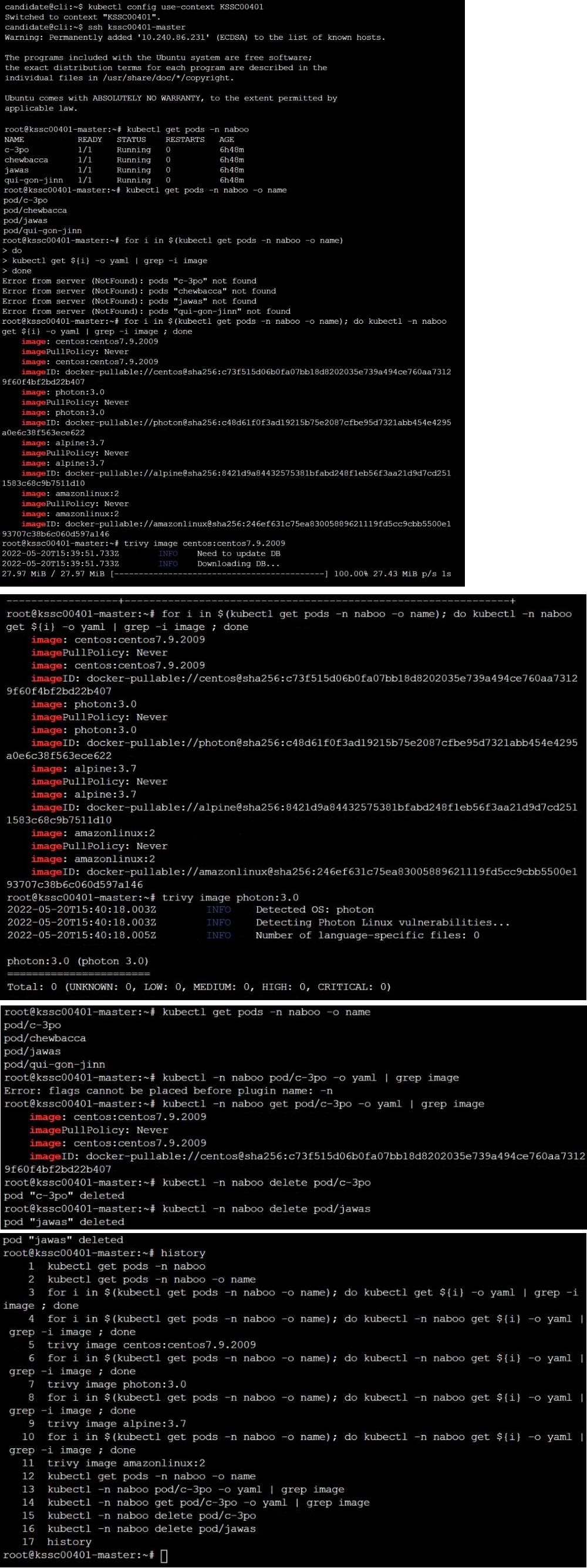
Question # 7
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context test-account
Task: Enable audit logs in the cluster.
To do so, enable the log backend, and ensure that:
- logs are stored at /var/log/Kubernetes/logs.txt
- log files are retained for 5 days
- at maximum, a number of 10 old audit log files are retained
A basic policy is provided at /etc/Kubernetes/logpolicy/audit-policy.yaml. It only specifies what not to log.
Note: The base policy is located on the cluster's master node.
Edit and extend the basic policy to log:
- Nodes changes at RequestResponse level
- The request body of persistentvolumes changes in the namespace frontend
- ConfigMap and Secret changes in all namespaces at the Metadata level
Also, add a catch-all rule to log all other requests at the Metadata level
Note: Don't forget to apply the modified policy. |
Explanation:
$ vim /etc/kubernetes/log-policy/audit-policy.yaml
uk.co.certification.simulator.questionpool.PList@11602760
$ vim /etc/kubernetes/manifests/kube-apiserver.yamlAdd these
uk.co.certification.simulator.questionpool.PList@11602c70
- --audit-log-maxbackup=10
Explanation[desk@cli] $ ssh master1[master1@cli] $ vim /etc/kubernetes/log-policy/auditpolicy.
yaml
apiVersion: audit.k8s.io/v1 # This is required.
kind: Policy
# Don't generate audit events for all requests in RequestReceived stage.
omitStages:
- "RequestReceived"
rules:
# Don't log watch requests by the "system:kube-proxy" on endpoints or services
- level: None
users: ["system:kube-proxy"]
verbs: ["watch"]
resources:
- group: "" # core API group
resources: ["endpoints", "services"]
# Don't log authenticated requests to certain non-resource URL paths.
- level: None
userGroups: ["system:authenticated"]
nonResourceURLs:
- "/api*" # Wildcard matching.
- "/version"
# Add your changes below
- level: RequestResponse
userGroups: ["system:nodes"] # Block for nodes
- level: Request
resources:
- group: "" # core API group
resources: ["persistentvolumes"] # Block for persistentvolumes
namespaces: ["frontend"] # Block for persistentvolumes of frontend ns
- level: Metadata
resources:
- group: "" # core API group
resources: ["configmaps", "secrets"] # Block for configmaps & secrets
- level: Metadata # Block for everything else
[master1@cli] $ vim /etc/kubernetes/manifests/kube-apiserver.yaml
apiVersion: v1
kind: Pod
metadata:
annotations:
kubeadm.kubernetes.io/kube-apiserver.advertise-address.endpoint: 10.0.0.5:6443
labels:
component: kube-apiserver
tier: control-plane
name: kube-apiserver
namespace: kube-system
spec:
containers:
- command:
- kube-apiserver
- --advertise-address=10.0.0.5
- --allow-privileged=true
- --authorization-mode=Node,RBAC
- --audit-policy-file=/etc/kubernetes/log-policy/audit-policy.yaml #Add this
- --audit-log-path=/var/log/kubernetes/logs.txt #Add this
- --audit-log-maxage=5 #Add this
- --audit-log-maxbackup=10 #Add this
output truncated
Linux Foundation CKS Exam Dumps
5 out of 5
Pass Your Certified Kubernetes Security Specialist (CKS) Exam in First Attempt With CKS Exam Dumps. Real Kubernetes Security Specialist Exam Questions As in Actual Exam!
— 48 Questions With Valid Answers
— Updation Date : 15-Apr-2025
— Free CKS Updates for 90 Days
— 98% Certified Kubernetes Security Specialist (CKS) Exam Passing Rate
PDF Only Price 49.99$
19.99$
Buy PDF
Speciality
Additional Information
Testimonials
Related Exams
- Number 1 Linux Foundation Kubernetes Security Specialist study material online
- Regular CKS dumps updates for free.
- Certified Kubernetes Security Specialist (CKS) Practice exam questions with their answers and explaination.
- Our commitment to your success continues through your exam with 24/7 support.
- Free CKS exam dumps updates for 90 days
- 97% more cost effective than traditional training
- Certified Kubernetes Security Specialist (CKS) Practice test to boost your knowledge
- 100% correct Kubernetes Security Specialist questions answers compiled by senior IT professionals
Linux Foundation CKS Braindumps
Realbraindumps.com is providing Kubernetes Security Specialist CKS braindumps which are accurate and of high-quality verified by the team of experts. The Linux Foundation CKS dumps are comprised of Certified Kubernetes Security Specialist (CKS) questions answers available in printable PDF files and online practice test formats. Our best recommended and an economical package is Kubernetes Security Specialist PDF file + test engine discount package along with 3 months free updates of CKS exam questions. We have compiled Kubernetes Security Specialist exam dumps question answers pdf file for you so that you can easily prepare for your exam. Our Linux Foundation braindumps will help you in exam. Obtaining valuable professional Linux Foundation Kubernetes Security Specialist certifications with CKS exam questions answers will always be beneficial to IT professionals by enhancing their knowledge and boosting their career.
Yes, really its not as tougher as before. Websites like Realbraindumps.com are playing a significant role to make this possible in this competitive world to pass exams with help of Kubernetes Security Specialist CKS dumps questions. We are here to encourage your ambition and helping you in all possible ways. Our excellent and incomparable Linux Foundation Certified Kubernetes Security Specialist (CKS) exam questions answers study material will help you to get through your certification CKS exam braindumps in the first attempt.
Pass Exam With Linux Foundation Kubernetes Security Specialist Dumps. We at Realbraindumps are committed to provide you Certified Kubernetes Security Specialist (CKS) braindumps questions answers online. We recommend you to prepare from our study material and boost your knowledge. You can also get discount on our Linux Foundation CKS dumps. Just talk with our support representatives and ask for special discount on Kubernetes Security Specialist exam braindumps. We have latest CKS exam dumps having all Linux Foundation Certified Kubernetes Security Specialist (CKS) dumps questions written to the highest standards of technical accuracy and can be instantly downloaded and accessed by the candidates when once purchased. Practicing Online Kubernetes Security Specialist CKS braindumps will help you to get wholly prepared and familiar with the real exam condition. Free Kubernetes Security Specialist exam braindumps demos are available for your satisfaction before purchase order. The Certified Kubernetes Security Specialist (CKS) exam,
offered by the Linux Foundation in collaboration with the Cloud Native
Computing Foundation (CNCF), is a performance-based certification designed to
validate a candidates expertise in securing Kubernetes environments. This
certification is essential for professionals looking to demonstrate their
skills in Kubernetes and cloud security, which are critical in todays
containerized application development and deployment ecosystems.
Exam Overview
The CKS exam tests candidates abilities in a real-world,
simulated environment. It requires candidates to solve multiple tasks from the
command line running Kubernetes. The exam is online, proctored, and lasts for
two hours. To be eligible for the CKS exam, candidates must first pass
the Certified Kubernetes Administrator (CKA) exam, ensuring
they have a foundational understanding of Kubernetes operations before focusing
on security.
Key Competencies and Domains
The CKS certification
covers many competencies for securing Kubernetes platforms and container-based
applications during build, deployment, and runtime. The exam content is
structured into several domains:
- Cluster Setup (10%): This
includes configuring network security policies, securing Kubernetes components
using CIS benchmarks, and setting up ingress objects with appropriate security
controls.
- Cluster Hardening (15%):
Candidates must demonstrate knowledge in restricting access to the Kubernetes
API, implementing Role-Based Access Control (RBAC), and minimizing the
permissions of service accounts.
- System Hardening (15%):
This involves reducing the attack surface by minimizing the host OS footprint,
using kernel hardening tools, and effectively managing IAM roles.
- Minimize Microservice
Vulnerabilities (20%): This domain manages Kubernetes secrets, sets up
OS-level security domains, and implements pod-to-pod encryption.
- Supply Chain
Security (20%): Candidates must know how to secure the supply chain by
validating and signing images, performing static analysis of workloads, and
scanning for vulnerabilities.
- Monitoring,
Logging, and Runtime Security (20%): This includes performing behavioral
analytics, detecting threats across various infrastructure layers, and ensuring
the immutability of containers at runtime.
Preparation and Resources
Candidates preparing for the CKS exam can benefit from a
variety of resources provided by RealBraindumps.
The curriculum for the CKS exam is open-sourced, enabling candidates to review
the material and align their preparation accordingly. Additionally,
RealBraindumps offers an exam simulator via Test Engine, allowing candidates to
familiarize themselves with the exam format and types of questions they might
encounter.
Benefits of Certification
Achieving the CKS
certification demonstrates a professional capability to secure Kubernetes
environments effectively. This certification is highly valued in the job
market, as it attests to a candidates comprehensive understanding of Kubernetes
security best practices. For organizations, hiring CKS-certified
professionals ensures that their Kubernetes deployments are secure,
scalable, and resilient to various security threats.
Send us mail if you want to check Linux Foundation CKS Certified Kubernetes Security Specialist (CKS) DEMO before your purchase and our support team will send you in email.
If you don't find your dumps here then you can request what you need and we shall provide it to you.
Bulk Packages
$50
- Get 3 Exams PDF
- Get $33 Discount
- Mention Exam Codes in Payment Description.
Buy 3 Exams PDF
$70
- Get 5 Exams PDF
- Get $65 Discount
- Mention Exam Codes in Payment Description.
Buy 5 Exams PDF
$100
- Get 5 Exams PDF + Test Engine
- Get $105 Discount
- Mention Exam Codes in Payment Description.
Buy 5 Exams PDF + Engine
 Jessica Doe
Kubernetes Security Specialist
We are providing Linux Foundation CKS Braindumps with practice exam question answers. These will help you to prepare your Certified Kubernetes Security Specialist (CKS) exam. Buy Kubernetes Security Specialist CKS dumps and boost your knowledge.
FAQs of CKS Exam
What
is the format of the Linux Foundation CKS Exam?
The
CKS exam is an online, proctored, performance-based test that requires
candidates to perform tasks on a command line within Kubernetes. Candidates
have 2 hours to complete these tasks. The exam tests various practices for
securing container-based applications and Kubernetes platforms during build,
deployment, and runtime. For more details, visit the Linux Foundation CKS Exam page.
How
can I register for the CKS Exam?
Register
for the CKS exam through the Linux Foundation's training portal. Before
scheduling the CKS exam, you must hold an active Certified Kubernetes
Administrator (CKA) certification.
What
are the prerequisites for taking the CKS Exam?
The
CKS exam requires candidates to have an active CKA certification. This ensures
that the candidate has sufficient knowledge of Kubernetes, which is crucial for
the specialized security exam.
What
topics are covered in the CKS Exam?
The
exam covers securing container-based applications and Kubernetes platforms,
including cluster setup, system hardening, supply chain security, and runtime
security. The Linux Foundation's certification page provides a comprehensive
breakdown of domains and competencies.
What
job roles benefit from CKS certification?
The
CKS certification is valuable for Kubernetes Administrators, Security
Specialists, DevOps Engineers, and Cloud Engineers looking to establish or
advance their careers in securing Kubernetes environments.
How
does CKS certification impact salary?
While
specific salary benefits can vary, the CKS
certification generally leads to higher pay and improved job prospects in
Kubernetes security. It demonstrates that advanced competency is highly valued
in tech and cybersecurity roles.
What
are the benefits of obtaining a CKS certification?
A
CKS certification validates a professional's expertise in critical security
practices for protecting Kubernetes environments. This certification is a
significant credential that can enhance a professional's credibility and
marketability.
How
accurate are RealBraindumps in providing the CKS exam dumps?
RealBraindumps
claims to offer accurate and up-to-date CKS
exam materials, which experts verify. However, candidates need to
cross-reference with official resources.
What
has been the positive feedback from users of RealBraindumps?
Users
of RealBraindumps often
commend the platform for the quality and relevance of the exam preparation
materials, which are frequently updated to reflect the latest exam formats and
questions.
Does
RealBraindumps offer any guarantees on their CKS exam dumps?
While
RealBraindumps provides materials it claims will help candidates pass on their
first try, users should advisable utilize the official
Linux Foundation materials and practice tests for the most reliable
preparation.
|
